TL;DR
- From pages to capabilities. We stop fetching documents and start procuring actions from agents.
- From search to negotiation. Your AI doesn’t “search”; it discovers, vets, quotes, contracts, executes, and audits other AIs.
- From domains to identities. Trust shifts from DNS/brands to cryptographic identities + verifiable reputation.
- From ads to meters. Economics move from attention markets to usage‑based settlement (per task, per token, per minute).
- From cookies to consent. Data access relies on purpose‑bound, revocable grants with machine‑readable policy.
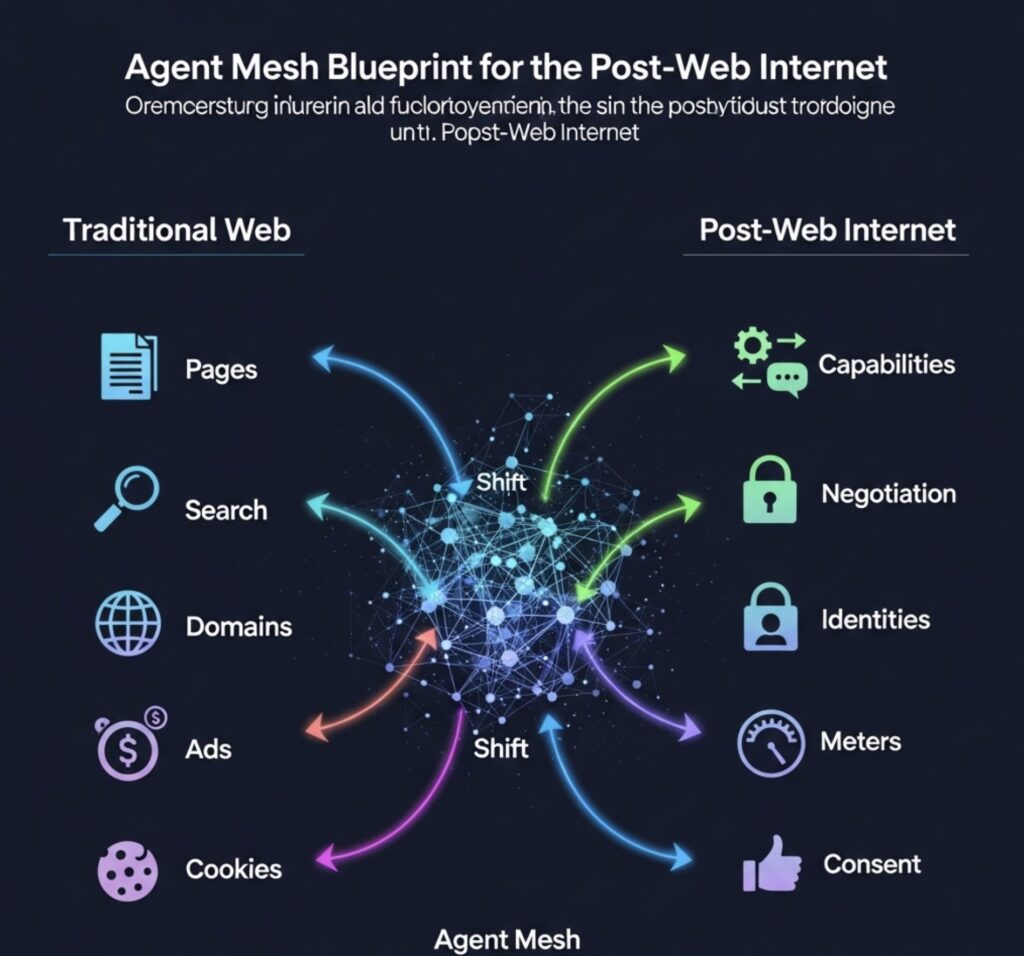
Mental Model: What Replaces Today’s Web Primitives?
| Today (Web) | Agent Mesh |
|---|---|
| URL | Agent ID (cryptographic DID-like identity) |
| HTML page | Capability (machine contract + schema) |
| Link graph | Reputation/attestation graph |
| Search engine | Discovery+Broker protocol |
| TLS | Mutual attestation + end‑to‑end encryption |
| Cookie | Verifiable consent token (scope, TTL, purpose) |
| Ads | Quotes & metered billing |
| SEO | Capability descriptors + outcome reliability |
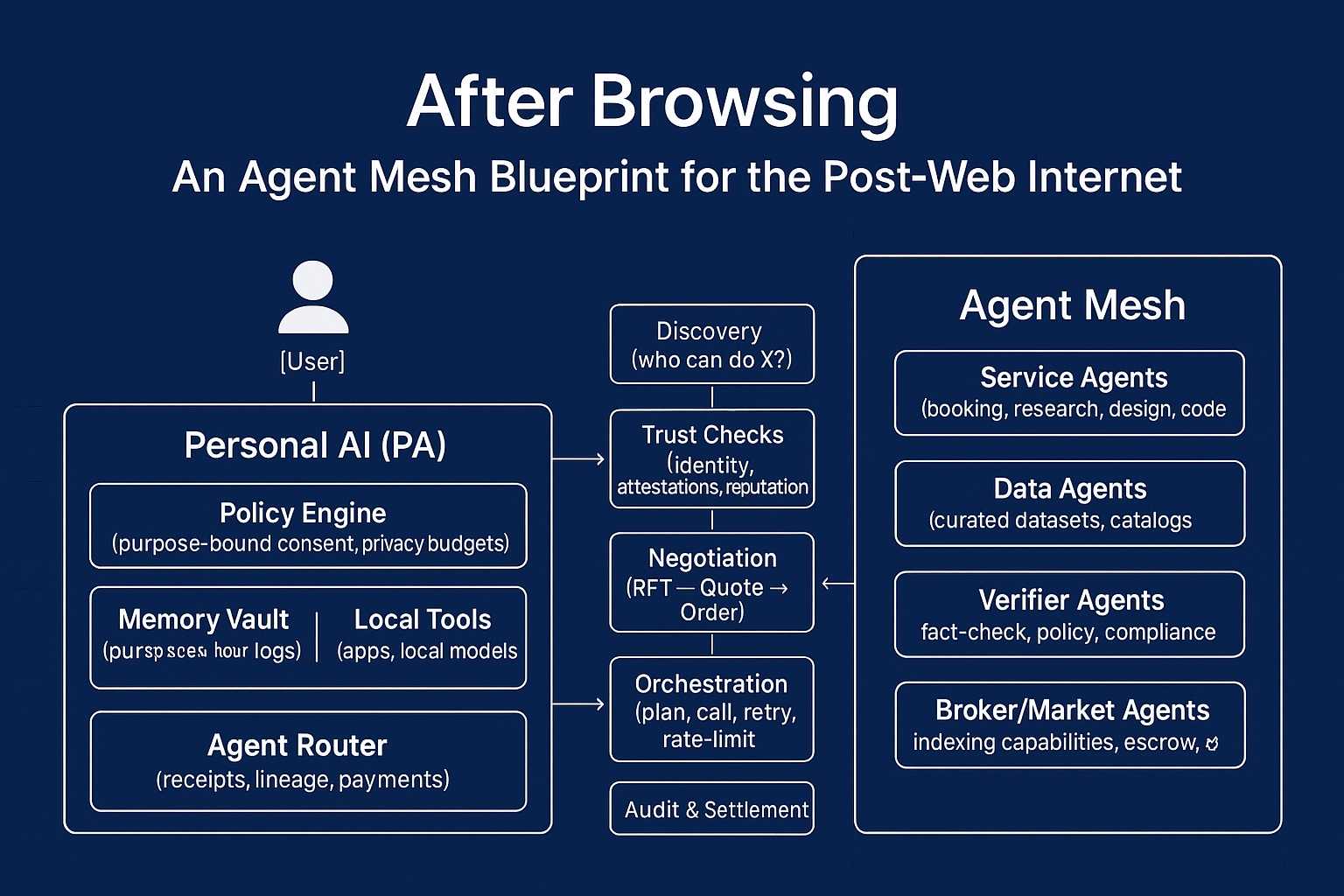
[You]
│
▼
Personal AI (PA)
├─ Policy Engine (what data can leave, for what purpose)
├─ Memory Vault (private knowledge, embeddings, logs)
├─ Tooling (local apps, devices, local LLMs)
└─ Agent Router
├─ Discovery (find candidate agents)
├─ Trust Check (identity, reputation, attestations)
├─ Negotiation (quotes, SLAs, data scopes)
├─ Orchestration (plan, call, rate-limit, retry)
└─ Audit/Settlement (receipts, lineage, payments)
Beyond your PA, the network comprises:
- Service AIs (search, code, design, travel, finance…)
- Data AIs (curated knowledge, catalogues, vertical expertise)
- Verifier/Observer AIs (fact‑checking, safety, policy compliance)
- Market/Broker AIs (indexing capabilities, facilitating escrow/settlement)
Core Protocol Primitives
- Identity & Trust
- Cryptographic agent IDs; verifiable credentials for claims (who runs this agent, what model, what policies).
- Remote attestation where possible (prove code/model env), or at least signed manifests + audits.
- Capability Description
- A machine‑readable manifest (OpenAPI‑like) describing:
capabilities(inputs/outputs, cost units, latency ranges)data use policy(purpose, retention, sharing)safety/guardrails(refuse lists, content classes)versioningand deprecation datesSLA tiersand pricing schedule
- A machine‑readable manifest (OpenAPI‑like) describing:
- Handshake & Consent
- Mutual identity proof → exchange purpose‑bound consent tokens (scope, TTL, PII classes).
- Optional: privacy budget (e.g., max tokens/records per task).
- Negotiation
- RFT (Request‑For‑Task) → Quote (price, SLA, risk, data requirements) → Order (binding) → Receipt (lineage).
- Transport & Data
- End‑to‑end encrypted messages; content‑addressed attachments (hashes) so results are deduped/verifiable.
- Store‑and‑forward tolerant of intermittent connectivity (LAN/mesh/offline first).
- Accounting
- Metered usage → settlement (credits, fiat, stable tokens, or bartered compute).
- Dispute & rollback hooks; insurance/bonding for high‑stakes tasks.
- Observability
- Provenance records (who did what with which data, when, under which policy).
- Model of Record tags to trace which model/version produced each artifact.
Minimal Message Shapes (example)
Agent Capability Manifest
{
"agent_id": "did:agent:gelato.v1",
"name": "Dridri Gelato Knowledge",
"version": "2025.08.14",
"capabilities": [
{
"id": "pairing.suggest",
"input_schema": {"flavor": "string", "diet": "enum[vegan, dairy]"},
"output_schema": {"suggestions": "array[string]"},
"cost": {"unit": "request", "price": 0.001},
"sla_ms_p50": 300
}
],
"data_policy": {"purpose": ["culinary_advice"], "retention": "none", "share": "no"},
"safety": {"nsfw": "block", "allergens": "warn"},
"attestations": ["signed:thorstenmeyerai.com"],
"reputation_refs": ["repute:cleanerslink:score:4.8"]
}
RFT (Request‑For‑Task)
{
"request_id": "rft-9d1",
"caller": "did:agent:personal.you",
"capability": "pairing.suggest",
"inputs": {"flavor": "pistachio", "diet": "dairy"},
"consent": {"purpose": "culinary_advice", "ttl": "5m"},
"constraints": {"max_price": 0.005, "deadline_ms": 800}
}
Quote
{
"request_id": "rft-9d1",
"agent_id": "did:agent:gelato.v1",
"price": 0.001,
"expected_latency_ms": 250,
"confidence": 0.88,
"policy_ack": true
}
Receipt (Provenance)
{
"request_id": "rft-9d1",
"outputs": {"suggestions": ["dark chocolate shards", "candied orange peel"]},
"lineage": [
{"model": "gelato-qa-3.2", "weights_hash": "…", "time": "2025-08-14T12:00:10Z"}
],
"data_use": {"retained": "no", "shared": "no"},
"signature": "ed25519:…"
}
Safety, Governance, and Failure Modes
- Purpose binding: data can only be used for the declared task; tokens expire; revocation lists enforced.
- Least‑data principle: your PA redacts, summarizes, or perturbs data (differential privacy where feasible).
- Rate limits & circuit breakers: stop cascading agent‑to‑agent storms.
- Verifier AIs: cross‑check critical outputs; insist on a second opinion over certain risk thresholds.
- Content and model drift: manifests carry sunset dates; your PA prefers agents with recent attestations.
- Adversarial resilience: reputation is multi‑source and cryptographically signed; no single authority.
Economic Models
- Per‑capability pricing: price per request/token/minute with clear SLAs.
- Subscriptions & retainers for steady workloads.
- Outcome‑based fees in some verticals (e.g., booking commission, lead conversion).
- Escrow/insurance for high‑stakes tasks (legal, medical, finance).
- Computation swaps: exchange cycles between AIs in closed loops (useful off‑grid).
What Discovery Looks Like (instead of SEO)
- Agents publish capability manifests + quality telemetry (success rates, latency, confidence).
- Brokers index manifests and reputations; your PA queries “who can do X with Y constraints?”
- Ranking signals: fresh attestations, delivery success under budget, dispute rate, and alignment with your policies (e.g., no data retention).
Making Your Properties “Agent‑Ready” (tailored to your projects)
You operate multiple knowledge sites (gelato, cleaning, style, narcissism recovery, etc.). To thrive in an agent world, ship Agent‑Readable Knowledge Capsules for each vertical:
- Package: each article → structured JSON (claims, sources, disclaimers), embeddings, and a tiny local retrieval model.
- Sign with your publisher key (DID); include version, scope, and license.
- Expose a manifest + 2–4 core capabilities per domain, e.g.
- DridriGelato:
pairing.suggest,batch.recipe.scale,allergen.check - Cleaners Link:
stain.remove.plan,eco.product.match - StyleGuru:
boho.palette.compose,room.layout.suggest
- DridriGelato:
- Policy: default
retention: none,share: no, and explicit liability statements. - Distribution: publish capsules to a P2P registry so PAs can fetch offline and cache locally.
- Reputation feed: expose anonymized performance stats (success %, avg latency) so brokers can rank you.
Net benefit: your knowledge becomes portable, signed, cacheable, and provable—useful even if the old web disappears.
Prototype Now (one‑week plan)
- Define IDs: generate publisher/agent keys for 2–3 demo agents.
- Author manifests: pick one capability per site and write the JSON manifest + policy.
- Local broker: a small service that ingests manifests and answers “who can X?” queries.
- Router in your PA: a function that takes a user goal → emits RFTs → collects quotes → enforces price/latency policies.
- Consent tokens: implement simple signed JWT‑like purpose tokens with TTL and scopes.
- Provenance receipts: every agent returns a signed receipt with model version and data‑use outcome.
- Verifier: a lightweight second‑opinion agent for factual claims.
- Cache: content‑address results on disk; prefer local results where freshness allows.
- Kill switch: rate limit and global abort on policy violations.
- Telemetry dashboard: show cost, agent mix, disputes, and provenance counts.
Offline/“Internet Went Away” Considerations
- LAN/mesh transport with store‑and‑forward; synchronize manifests/results opportunistically (“sneakernet” acceptable).
- Model updates as signed deltas; PAs refuse stale models past their sunset date.
- Content addressing means deduped storage and verifiable integrity without central servers.
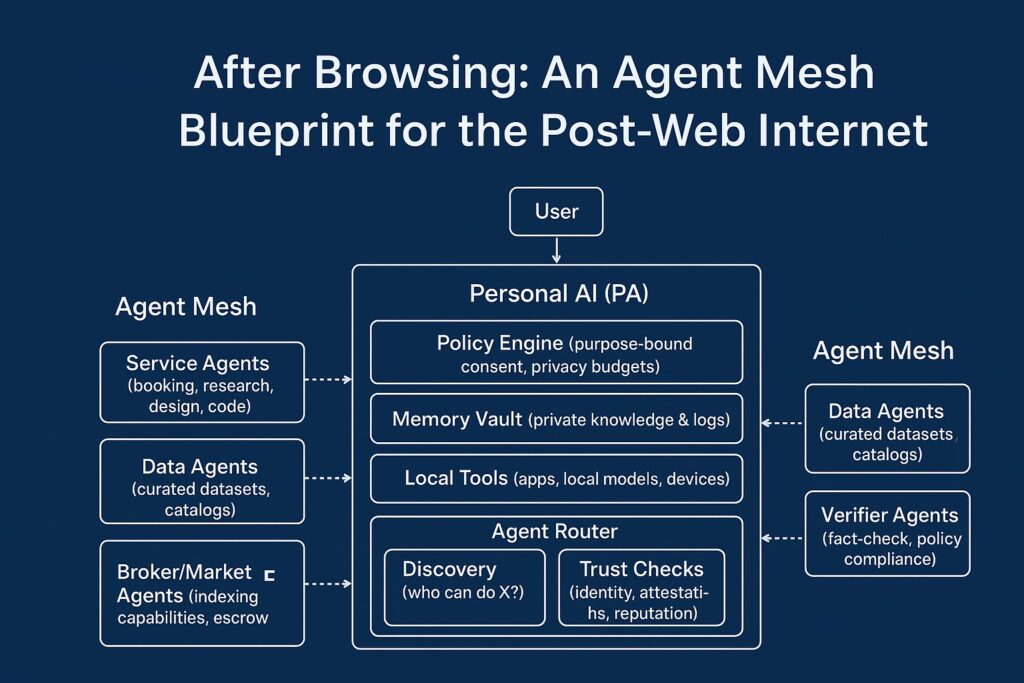
Option B — ASCII diagram (always works)
[User]
│
▼
Personal AI (PA)
├─ Policy Engine (purpose-bound consent, privacy budgets)
├─ Memory Vault (private knowledge & logs)
├─ Local Tools (apps, local models, devices)
└─ Agent Router
├─ Discovery (who can do X?)
├─ Trust Checks (identity, attestations, reputation)
├─ Negotiation (RFT → Quote → Order)
├─ Orchestration (plan, call, retry, rate-limit)
└─ Audit & Settlement (receipts, lineage, payments)
Agent Mesh (outside the PA)
├─ Service Agents (booking, research, design, code)
├─ Data Agents (curated datasets, catalogs)
├─ Verifier Agents (fact-check, policy, compliance)
└─ Broker/Market Agents (indexing capabilities, escrow, dispute)
What Replaces Today’s Web Primitives
| Today (Web) | Agent Mesh Equivalent |
|---|---|
| URL | Agent ID (DID‑like cryptographic identity) |
| HTML page | Capability (machine‑readable manifest + schema) |
| Link graph | Reputation/attestation graph |
| Search engine | Discovery + Broker protocol |
| TLS | Mutual attestation + e2e encryption |
| Cookie | Purpose‑bound consent token (TTL, scope) |
| Ads | Quotes & metered billing |
| SEO | Reliability & policy conformance signals |
Minimal Message Shapes (copy/paste)
Use these as canonical examples for manifests, consent, negotiation, and provenance.
1) Agent Capability Manifest
{
"agent_id": "did:agent:thorstenmeyerai.demo",
"name": "Thorsten Meyer AI — Demo Agent",
"version": "2025.08",
"capabilities": [
{
"id": "research.summarize",
"input_schema": {"topic": "string", "length": "enum[short,medium,long]"},
"output_schema": {"summary": "string", "citations": "array[string]"},
"pricing": {"unit": "request", "price": 0.002},
"sla_ms_p50": 400,
"deprecation_date": "2026-02-01"
}
],
"data_policy": {"purpose": ["research"], "retention": "none", "share": "no"},
"safety": {"nsfw": "block", "medical": "warn"},
"attestations": ["signed:thorstenmeyerai.com@2025-08-15"],
"reputation_refs": ["repute:mesh:score:4.8:2025Q3"]
}
2) Purpose‑Bound Consent Token (grant)
{
"subject": "did:agent:personal.user",
"audience": "did:agent:thorstenmeyerai.demo",
"purpose": "research",
"scopes": ["read:provided_docs"],
"ttl": "10m",
"retention": "none",
"nonce": "c6a1…",
"signature": "ed25519:…"
}
3) Negotiation: RFT → Quote → Order
{
"rft": {
"request_id": "rft-001",
"capability": "research.summarize",
"inputs": {"topic": "agentic internet", "length": "medium"},
"constraints": {"max_price": 0.01, "deadline_ms": 1200},
"consent_ref": "grant:c6a1…"
},
"quote": {
"request_id": "rft-001",
"price": 0.003,
"expected_latency_ms": 350,
"confidence": 0.86,
"policy_ack": true
},
"order": {
"request_id": "rft-001",
"accept_quote": true
}
}
4) Receipt & Provenance
{
"request_id": "rft-001",
"outputs": {"summary": "…", "citations": ["…"]},
"lineage": [
{"model": "tm-research-3.1", "weights_hash": "sha256-…", "time": "2025-08-15T10:42:00Z"}
],
"cost": {"price": 0.003, "tokens_in": 1200, "tokens_out": 350},
"data_use": {"retained": "no", "shared": "no"},
"signature": "ed25519:…"
}
Design Patterns That Actually Matter
- Least‑Data Invocation
Redact, summarize, or mask by default. Expand only on need; enforce privacy budgets (max records/tokens per task). - Two‑Agent Rule for Risk
For health/finance/legal tasks, require a verifier agent to concur or escalate to a human. - Sunset by Default
Manifests and models carry deprecation dates; your router prefers fresh attestations. - Deterministic “Model of Record”
Tag important artifacts with(model, weights_hash, time)for auditability and reproducibility. - Circuit Breakers
Cap fan‑out, per‑task spend, and latency to prevent agent storms.
New Economics (beyond ads)
- Per‑capability metering: price per request/minute/token with clear SLAs.
- Subscriptions/retainers for steady workloads.
- Outcome pricing in verticals (e.g., booking commission).
- Escrow/insurance for high‑stakes tasks.
- Compute swaps within trusted circles when currency rails are constrained.
30–60–90 Day Implementation Plan
Days 1–30 — Foundations
- Issue publisher keys (DIDs) for two demo agents.
- Publish v1 manifests with
retention: noneand explicit purposes. - Build a local broker answering “who can do X under Y constraints?”
- Implement purpose‑bound consent tokens (short TTL, revocable).
Days 31–60 — Orchestration & Safety
- Ship the RFT → Quote → Order → Receipt flow.
- Add a verifier agent for medium‑to‑high‑risk tasks.
- Wire circuit breakers (max fan‑out, spend, latency).
- Start provenance logs and a minimal dashboard (success %, dispute rate, cost).
Days 61–90 — Productization
- Convert 3–5 cornerstone articles into signed knowledge capsules (claims, schemas, disclaimers).
- Expose 2 capabilities per domain; test offline cache (content‑addressed results).
- Launch pricing/SLA experiments; document policy and revocation endpoints.
Applying This to Thorsten Meyer AI Properties (examples)
- Dridri Gelato →
pairing.suggest,recipe.scale,allergen.check - Cleaners Link →
stain.plan,eco.product.match,checklist.generate - StyleGuru →
boho.palette.compose,room.layout.suggest - Narcissistic Man →
boundary.script.generate,safety.plan(with clear disclaimers)
Each capability ships with: input/output schema, price/SLA, safety scope, purpose policy, version, deprecation date, and attestations.
FAQ
Is this just “using APIs”?
No. Agents expose negotiable capabilities with policy and provenance, and can refuse outside authorized purposes.
Can this work offline?
Yes. Use LAN/mesh with store‑and‑forward; cache signed manifests and content‑addressed results; enforce attestation freshness when connectivity returns.
How do we keep costs sane?
Rank candidates by expected cost‑to‑success; cap fan‑out and per‑task budgets; prefer agents with proven delivery under budget.